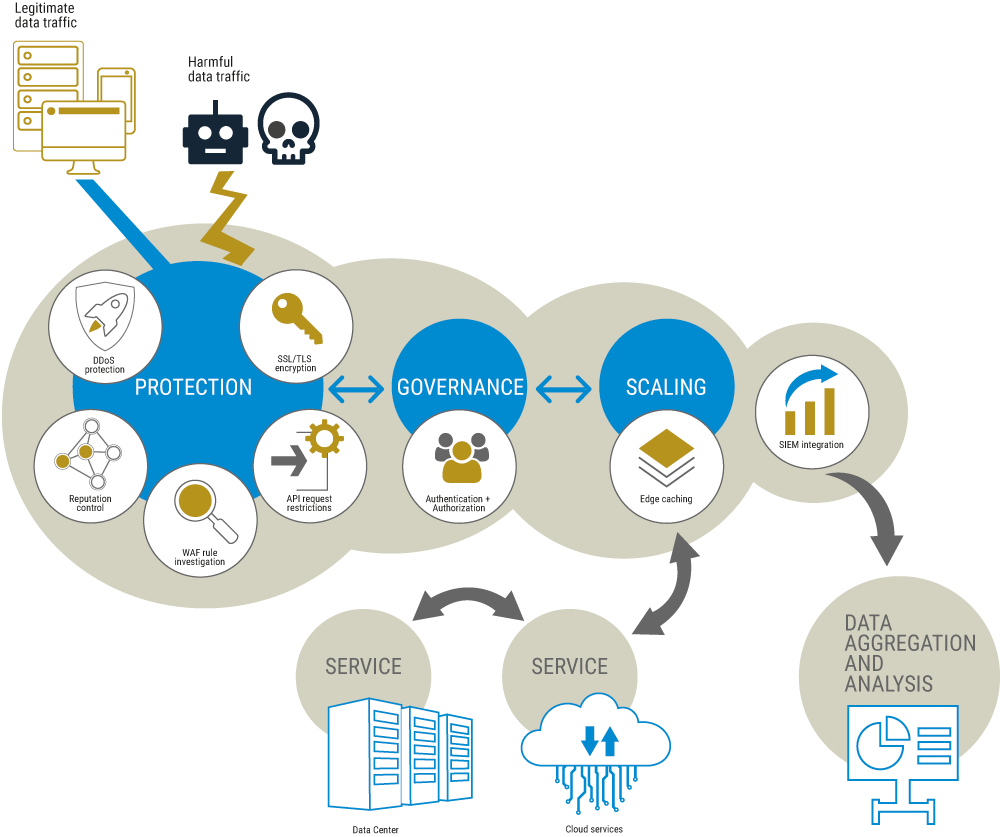
Web Application
And
API Protection
WAAP: Essential for e‑commerce
Not only online stores are very active on Black Friday and Cyber Monday, hackers also try to illegally secure a slice of the cake. According to analyses by Link11, companies were hit five times more often with DDoS attacks on Cyber Weekend 2023 than in the previous year. The terabit threshold in malicious data traffic has already been exceeded. In addition, security service providers registered targeted attacks on e-commerce providers, payment service providers and logistics companies in order to cause the greatest possible damage and attack applications and online services with comparatively few resources on days that were generally already experiencing peak loads due to the campaigns.
So-called WAAP solutions (Web application and API protection) offer comprehensive protection, providing many solutions for the security of your web applications and APIs, from DDoS defense and web application firewalls to bot management. Metaways supports you with the onboarding, support and management of the security solutions so that you can focus on the further development of your software and your core competence: Our experienced admins and project managers accompany your project through the entire pre-prod phase right up to going live and also take responsibility for your web protection during regular operation – from support to managed service. We work together with two of the leading providers of WAAP products and can advise you which solutions promise the best results for your needs.
FAQ
Display none
Eigentlich jede Firma, die auf die kontinuierliche Verfügbarkeit ihrer Web-Applikationen angewiesen ist. Die Ziele von DDoS-Attacken sind unvorhersehbar, die Gründe der Hacker vielfältig: In einigen Fällen geht es um sogenannten Hacktivismus, häufiger um Erpressung, digitale Kriegsführung oder bösartigen Schabernack.
Für Unternehmen gibt es also gute Gründe, sich vor den Angriffen zu schützen.
Verfügbarkeit gewährleisten: DDoS-Angriffe zielen darauf ab, die Verfügbarkeit von Online-Diensten zu beeinträchtigen. Ein erfolgreicher Angriff kann zu Ausfallzeiten führen, was finanzielle Verluste und Reputationsschäden verursachen kann.
Datensicherheit: DDoS-Angriffe dienen oft als Ablenkung, um Sicherheitsinfrastrukturen zu überlasten, während gleichzeitig andere Angriffe, wie zum Beispiel Datenexfiltration, durchgeführt werden. Ein effektiver DDoS-Schutz kann helfen, solche Angriffe zu verhindern.
Reputationsschutz: Wenn Kunden feststellen, dass ein Unternehmen aufgrund von DDoS-Angriffen nicht erreichbar ist, kann dies das Vertrauen beeinträchtigen und die Reputation schädigen.
Gesetzliche Anforderungen: In einigen Branchen gibt es gesetzliche Vorschriften, die Unternehmen dazu verpflichten, angemessene Sicherheitsvorkehrungen zu treffen, um ihre Daten und Dienste zu schützen. DDoS-Schutz kann dabei eine Rolle spielen.
Es gibt verschiedene Methoden, um sich vor DDoS-Attacken auf den Layern 4-7 zu schützen, darunter die Verwendung von Content Delivery Networks (CDNs), Web Application Firewalls (WAFs) und spezialisierten DDoS-Schutzdiensten. Es ist wichtig, eine umfassende Sicherheitsstrategie zu entwickeln und regelmäßig zu aktualisieren, um auf die sich entwickelnden Bedrohungen zu reagieren.
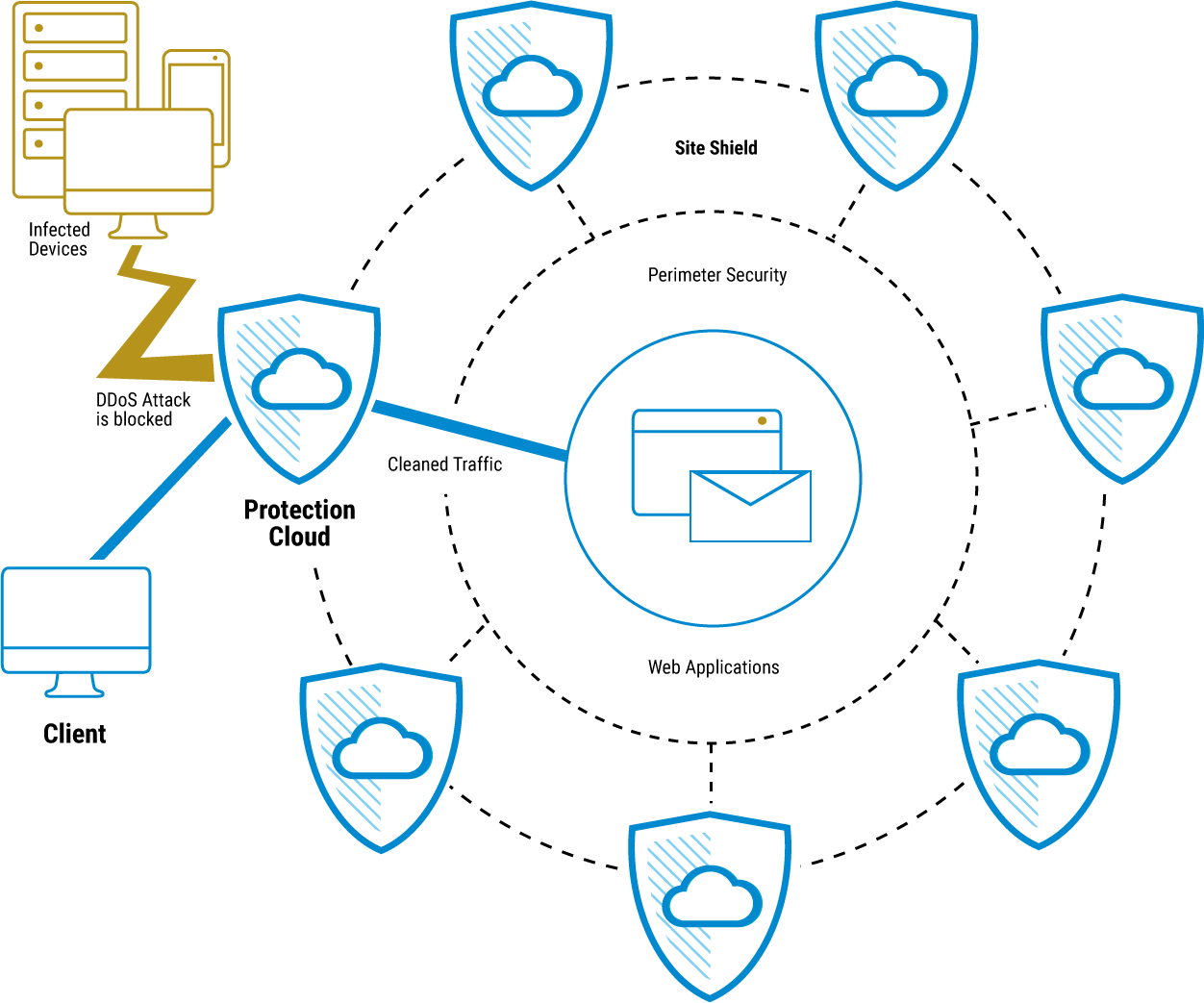
Who needs web DDoS protection?
Any company that relies on the continuous availability of its web applications. The targets of DDoS attacks are unpredictable, and the hackers’ reasons are varied: in some cases it is a case of so-called hacktivism, more often blackmail, digital warfare or malicious pranks.
There are therefore good reasons for companies to protect themselves against attacks.
Ensure availability: DDoS attacks aim to impair the availability of online services. A successful attack can lead to downtime, which can cause financial losses and reputational damage.
Data security: DDoS attacks often serve as a distraction to overload security infrastructures while other attacks, such as data exfiltration, are carried out at the same time. Effective DDoS protection can help prevent such attacks.
Reputation protection: If customers find that a company is unavailable due to DDoS attacks, this can affect trust and damage reputation.
Legal requirements: In some industries, there are legal requirements that oblige companies to take appropriate security precautions to protect their data and services. DDoS protection can play a role in this.
There are various methods to protect against DDoS attacks at layers 4-7, including the use of content delivery networks (CDNs), web application firewalls (WAFs) and specialized DDoS protection services. It is important to develop and regularly update a comprehensive security strategy to respond to evolving threats.
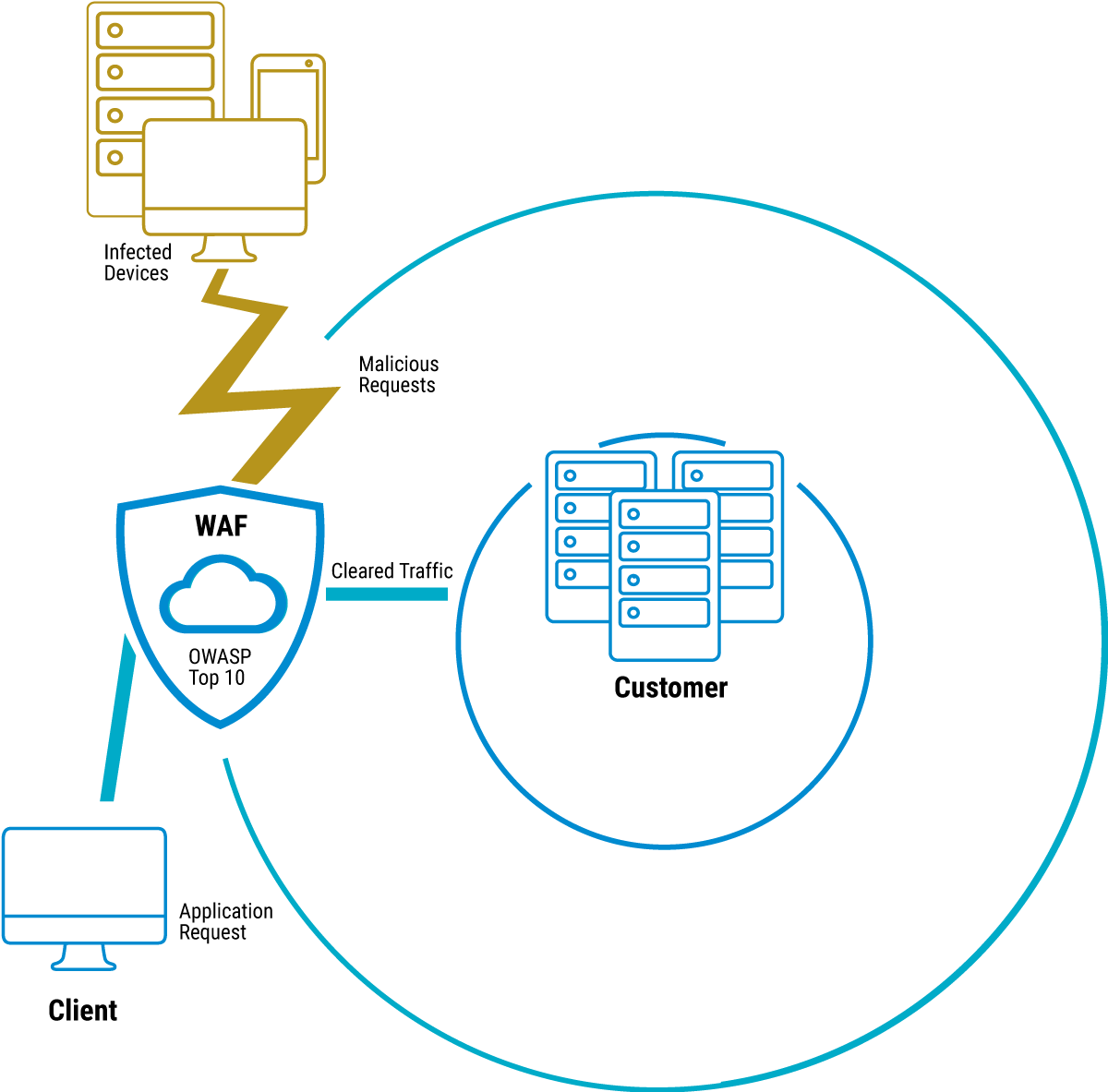
What are the benefits of a web application firewall?
A web application firewall (WAF) is a security solution designed to protect web applications from various types of cyberattacks. Some advantages and functions that a web application firewall can offer are
Protection against application layer attacks: a WAF is designed to protect applications at the application layer of the OSI reference model. It detects and blocks specific attack patterns, such as SQL injections, cross-site scripting (XSS), cross-site request forgery (CSRF) and other attacks targeting the application layer.
Filtering malicious traffic: A WAF analyzes incoming and outgoing traffic and filters out malicious content. This allows malicious payloads, malware and other threats to be blocked before they reach the web application.
Protection against DDoS attacks: Some WAF solutions also provide protection against Distributed Denial of Service (DDoS) attacks. They can monitor data traffic and recognize suspicious patterns in order to identify and ward off an attack.
Security rules and policies: WAFs allow admins to set custom security policies and rules. This allows fine-tuned control over which traffic is allowed and which requests should be considered potentially dangerous.
Virtual patching: If security vulnerabilities exist in the web application, a WAF can serve as a virtual patch to close these vulnerabilities until the actual application can be updated or patched.
Logging and monitoring: A WAF often provides logging and monitoring capabilities that make it possible to track suspicious activity, analyze attacks and take appropriate action.
Compliance fulfillment: Web application firewalls can help organizations meet industry and regulatory compliance requirements by implementing security policies and controls.
Overall, a web application firewall helps to increase web application security, minimize vulnerabilities and defend against application layer attacks. However, it is important to note that WAFs should be a part of a comprehensive security strategy that also includes regular security audits, patch management and security awareness training.
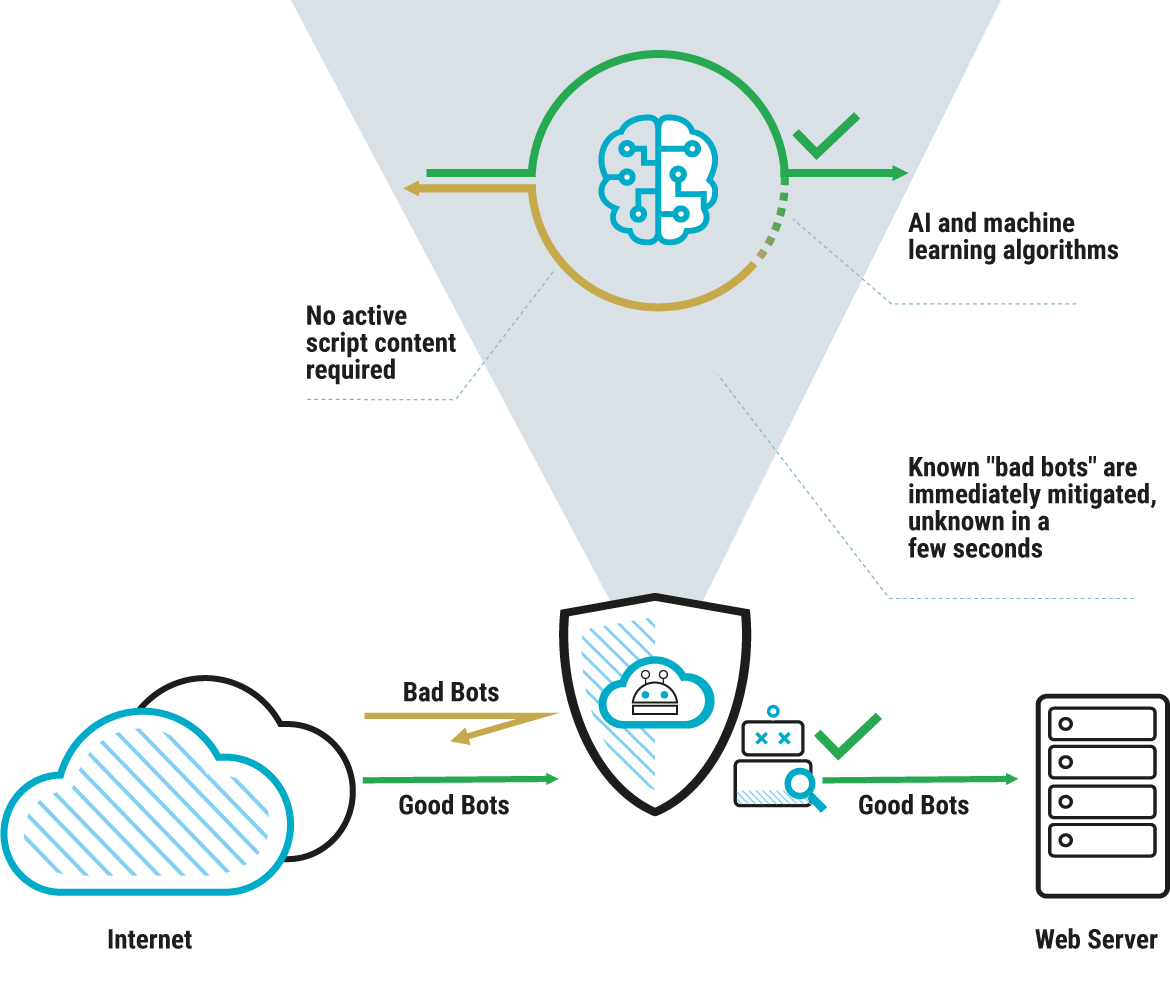
When does bot mitigation take effect?
Protection against DDoS attacks: Bot management systems can be used to detect and defend against Distributed Denial of Service (DDoS) attacks, where a large number of bots attempt to overload a website or application simultaneously.
Identification of malicious bots: Some bots may have malicious intentions, such as web scraping, data theft, fraud or bypassing security measures. Bot mitigation helps to identify and block such harmful bots.
Prevention of scraping: Web scraping bots can be used to extract large amounts of data from a website, which is detrimental to server capacity and bandwidth. Bot management can identify and control such scraping activities.
Protection against bots in online transactions: In e-commerce platforms or other systems that enable online transactions, bot management can be used to ensure that real users are using the services and automated bots are not being used for fraudulent activities.
The implementation of bot management systems can vary depending on the specific requirements of an organization. They can be based on various technologies, including machine learning, behavioral analysis, IP filtering and captchas. The aim is to protect the integrity, availability and security of online resources.
What does the DNS do and what are the benefits of optimization?
The Domain Name System (DNS) is a basic protocol on the Internet that is used to convert human-friendly domain names (such as www.example.com) into numerical IP addresses (such as 192.168.1.1), which are used by computers to identify each other on the network.
Optimizing the DNS can provide several benefits:
Faster load times: By optimizing the DNS, queries can be resolved faster. This results in shorter waiting times for users when they visit a website or access other resources on the internet.
Improved reliability: Efficient DNS optimization can improve the availability of resources by ensuring that DNS requests are processed reliably and correctly. This helps to minimize downtime.
Load balancing: DNS optimization can help distribute the load on different servers by redirecting queries to appropriate servers. This improves the utilization and scalability of servers.
Security: An optimized DNS can provide security features such as blocking malicious domains or detecting DNS-based attacks to protect the integrity of the network.
Globally distributed queries: By implementing content delivery networks (CDNs) and anycast networks, an optimized DNS configuration can route queries to geographically distributed servers to minimize latency and deliver content closer to end users.
Several approaches can be taken to optimize DNS, including the use of fast DNS servers, caching strategies, implementing load balancing and the use of DNS anycast networks.
What advantages do I have if I use the managed service from Metaways?
On the one hand, we offer you some exclusive packages from web security specialists that are only available from partners such as Metaways. Secondly, you benefit from our many years of expertise in the secure and protected operation of web applications.
Metaways knows the individual settings and configurations in the web security products and thus saves you the initial training effort and, in the further course, resources that would have to be devoted to the setup and ongoing maintenance.
Can you take over the management yourself?
That is possible. In this case, Metaways provides access to the web security products and also provides support if you need it.
Does my application have to be hosted by Metaways?
We can also launch and manage a WAAP solution for you if you have your application hosted by another provider. However, this results in detours in communication, which can lead to delayed problem solutions, because our admins then sometimes have to communicate with the hoster in order to be able to rule out a cause on the hosting side in the event of access problems.
Our partner
Link11
Link11 is a specialized European IT security provider and protects infrastructures and web applications from cyber attacks. The company is headquartered in Germany and has offices worldwide in Europe, North America, Asia and the Middle East. Its cloud-based IT security solutions help companies to strengthen the cyber resilience of their networks and critical applications and avoid business disruptions.
Link11’s product portfolio includes a wide range of cloud-based IT security solutions such as DDoS protection for infrastructure and applications, web application firewall, bot mitigation, secure DNS and secure CDN. According to the consensus of analysts (Frost & Sullivan, Gartner and others), Link11 offers high-quality protection of all relevant OSI layers and against all forms of DDoS attacks, including unknown ones, within seconds.
The technological basis for this is Link11’s patented DDoS protection, which relies on machine learning and consistent automation. Link11’s own global multi-terabit network with currently 42+ PoPs (Points Of Presence), which connects the DDoS filter clusters, is monitored around the clock by the Link11 Security Operations Center.
The German Federal Office for Information Security (BSI) recognizes Link11 as a qualified provider of DDoS protection for critical infrastructure. With ISO 27001 certification, the company meets the highest standards in data security. Since the company was founded in 2005, Link11 has received numerous awards for its innovative solutions and business development.
Our partner
Akamai
Akamai Technologies, Inc. is a global provider of content delivery network (CDN) and cloud services. The company was founded in 1998 and is headquartered in Cambridge, Massachusetts, USA. Its primary business is to accelerate and secure content and applications for enterprises across its global network of servers and data centers.
Akamai operates one of the largest content delivery networks in the world and offers a variety of services including web performance optimization, security, media delivery, cloud computing services and more. Their solutions are used by organizations to improve the availability, speed and security of their online content and applications.
Akamai Connected Cloud – the highly distributed edge and cloud platform – makes it easier for organizations to develop and run applications and workloads while bringing experiences closer to users and keeping threats at bay. That’s why innovative organizations around the world rely on Akamai to create, deliver and protect their digital experiences.
Its leading cloud computing, security and content delivery services help global organizations make life better for billions of people, billions of times a day.
Produkte
DDoS Protection
Bot
Mitigation
Web DDos
Protection
API
Protection
Web Application
Firewall
DNS
Protection
Vorteile

Adaptive security with proactive self-optimization

Intelligent functions and machine learning for traffic analysis

Improved administrability thanks to user-friendly interfaces and zero-touch principle

DDoS protection that responds to application-level attacks within seconds

Metaways managed services and 24×7 admin support

Hosting and web application and API protection from a single source

24×7 Metaways support

Guaranteed SLA for WAAP and Metaways managed services

Effective protective measures against the risks of the OWASP
Top 10
Curious?
+49 40 31 70 31 – 65
Metaways
Infosystems
GmbH
Address
Pickhuben 2
20457 Hamburg
Germany
Telephone
+49 40 31 70 31-0
